Authentication is at the core of secure financial APIs. Since our platform connects services across accounting, invoicing, e-commerce, point of sale, and more, it’s essential to ensure that every request comes from a verified and trusted source. The software we connect to use a variety of authentication methods (OAuth 2.0, API keys, username/password, and proprietary token schemes). Chift abstracts that complexity and handles authentication end-to-end so activation stays smooth for your users, often in just one click.
Different authentication methods have different strengths, trade-offs, and implementation considerations. In this article, we’ll review the most common approaches we use, highlighting how they work, their advantages and disadvantages, and best practices for applying them in real-world integrations.
OAuth 2.0
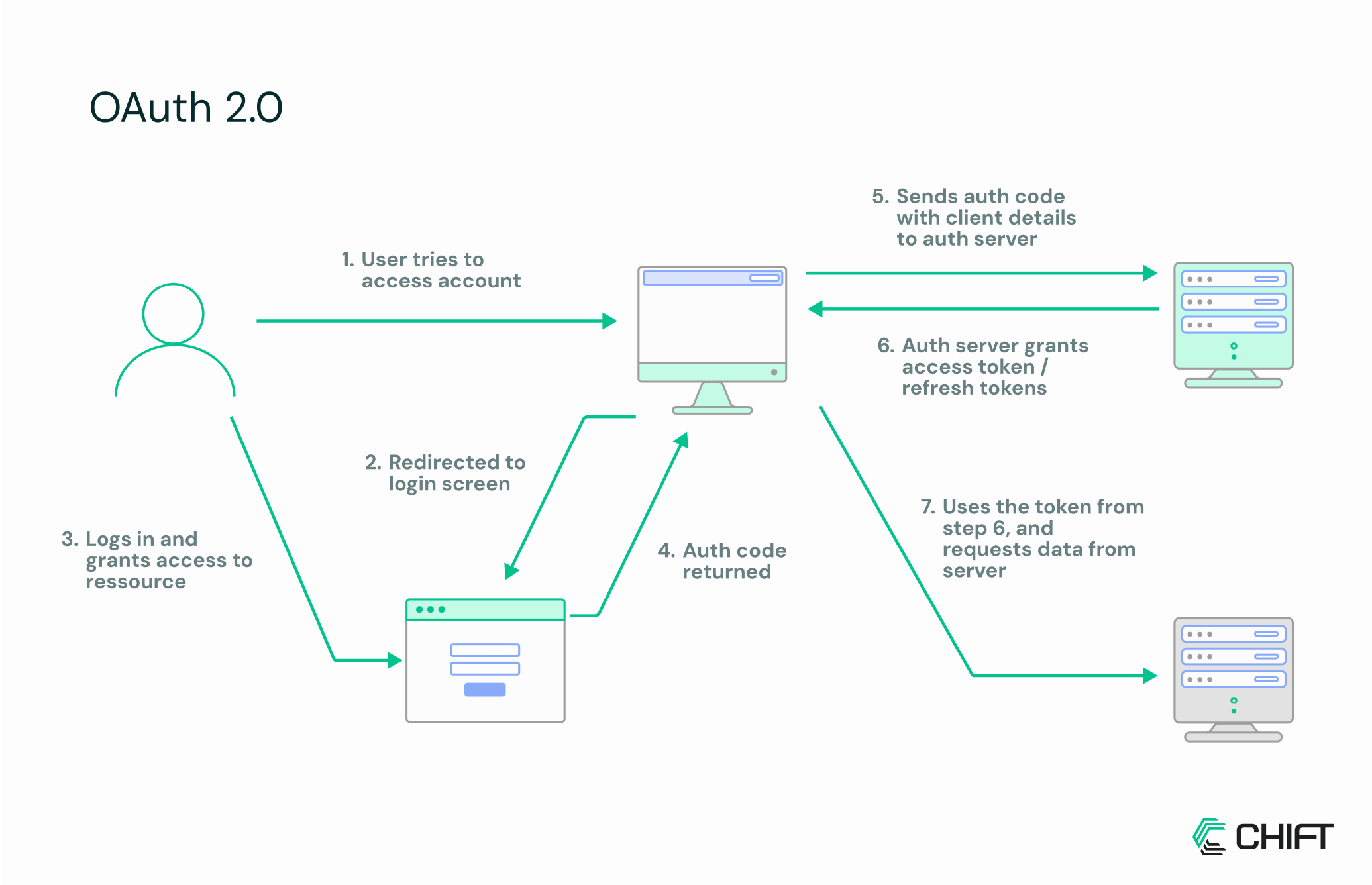
OAuth 2.0 has become the industry standard for delegating access to APIs without exposing user credentials. Instead of passing around a username and password, a user authorizes an application to act on their behalf and receives a token that represents specific permissions. This shift is especially important in financial services, where sensitive data is exchanged between many different platforms.
In practice, OAuth makes integrations safer and more flexible. A merchant can connect their e-commerce store to an accounting platform, or grant a payment provider temporary access, without ever handing over their login details. The system issues tokens with limited scopes, so each application only gets the access it really needs.
That said, OAuth isn’t yet the default everywhere. Many APIs, including some in our ecosystem, are still transitioning away from simpler methods like API keys. This means developers often have to handle a mix of approaches, depending on the provider.
Pros
- Credentials never shared with third-party apps.
- Fine-grained control of access via scopes.
- Aligned with PSD2 and Open Banking standards.
Cons
- More complex to implement than alternatives.
- Different flows (Authorization code, Client credentials, etc.) can be confusing.
- Requires secure handling and rotation of tokens.
Best practices
- Keep scopes limited to the minimum required.
- Validate redirect URIs and the state parameter to prevent CSRF.
- Store tokens securely and refresh them only on a trusted backend.
Keys out, tokens in
Old-school API keys are fading fast. More and more financial platforms, from accounting to e-commerce, are adopting OAuth 2.0 for token-based, scoped access that’s safer and easier to manage for developers.
API keys
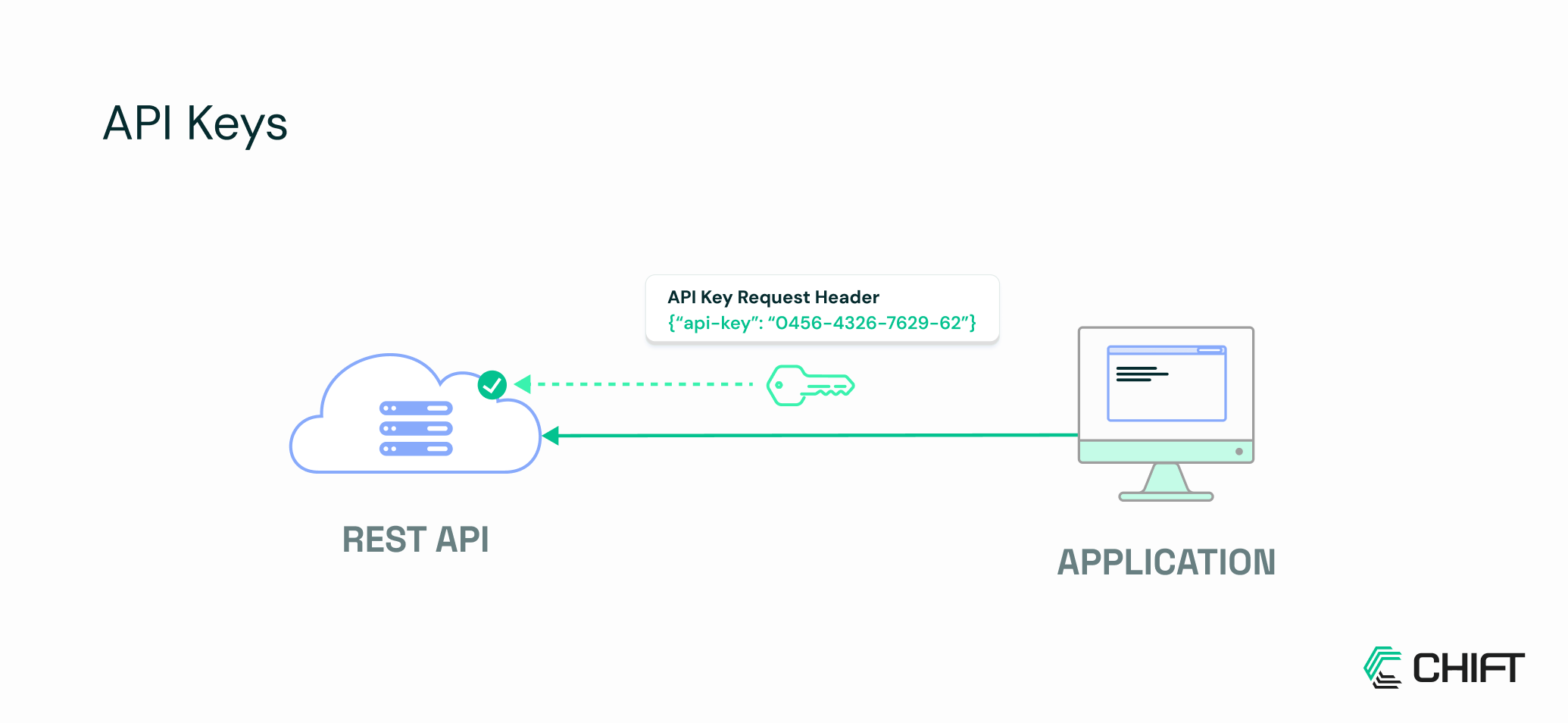
While OAuth 2.0 is on the rise, many platforms still rely on simpler authentication: API keys. A unique string of characters that identifies your application, acting like a password, granting access to the API without the complexity of token exchanges or scopes. For developers, API keys are easy to implement and integrate, which is why they remain common, especially for server-to-server interactions or internal apps.
However, simplicity comes at a cost. API keys are long-lived and often have broad access, so if they’re exposed, anyone can use them. Unlike OAuth tokens, they don’t inherently limit permissions or offer delegated access, which can make them less secure in multi-application ecosystems. Want to learn more about API keys? Check this article from IBM.
Pros
- Very easy to implement and use.
- No need for complex flows or token handling.
- Well-suited for server-to-server integrations.
Cons
- Credentials are static and can be misused if leaked.
- No fine-grained access control; usually all-or-nothing.
- Harder to rotate securely without downtime.
Best practices
- Limit the permissions associated with each key.
- Store keys securely, never in client-side code.
- Rotate keys regularly and immediately revoke compromised ones.
- Use environment variables or secret managers for storage.
Handle with care
API keys are the quick-and-easy pass to your API, but one slip and you’re handing the door to anyone. Treat them like a VIP badge: fast access, but don’t lose it.
Username & password
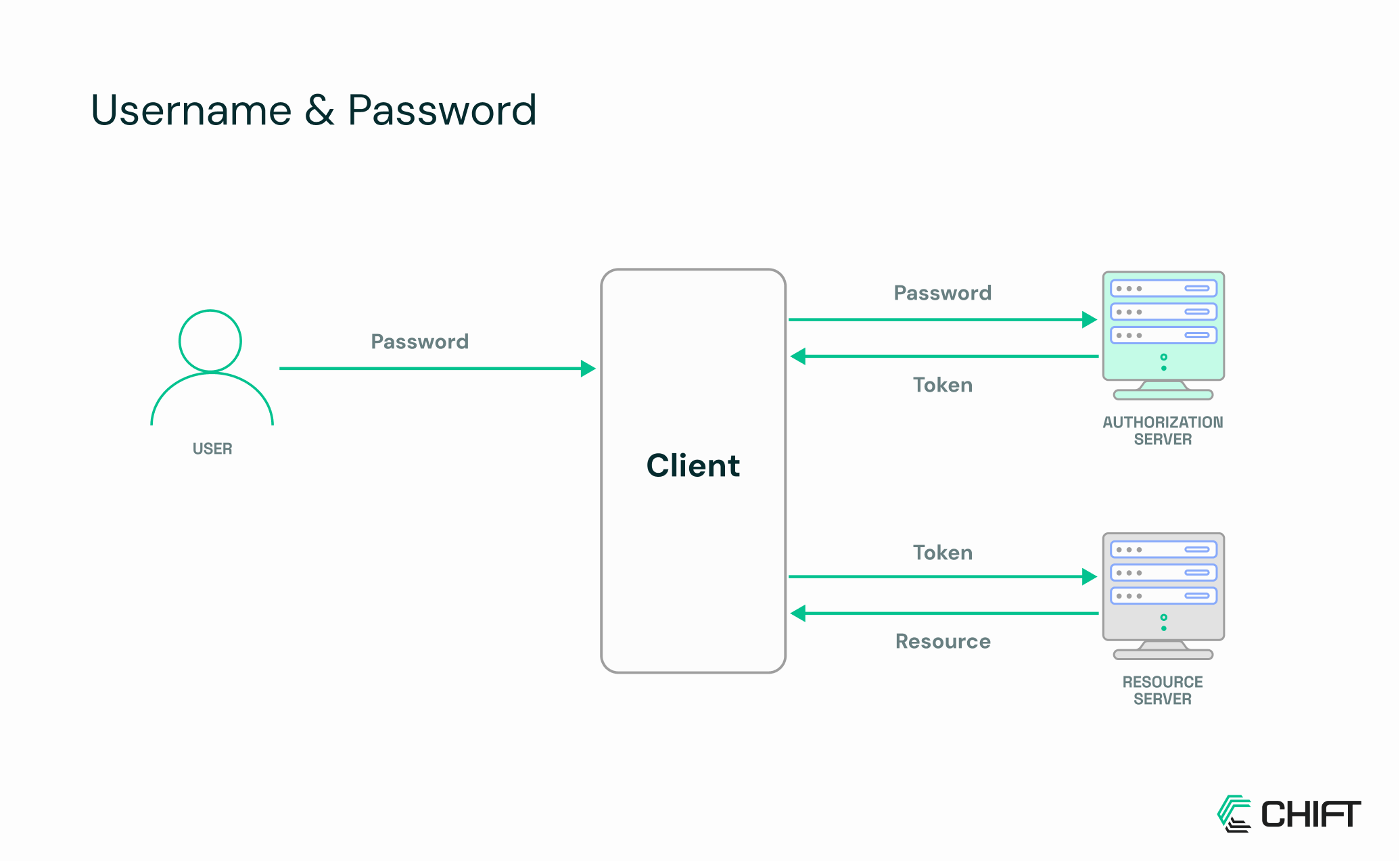
Username and password authentication is the classic approach: your application directly sends a user’s credentials to the API to gain access. It’s simple, familiar, and doesn’t require token management, making it easy for quick integrations or smaller internal tools. Many legacy systems and smaller financial platforms still rely on this method, especially where OAuth or API keys aren’t yet implemented.
Unlike API keys or OAuth tokens, username and password credentials often grant access not only to the API but also to the software’s user interface. This can make integrations more powerful, but also more sensitive, any leaked credentials could compromise both programmatic and manual access. Multi-factor authentication (MFA) can help mitigate this risk, adding an extra layer of protection when available.
Pros
- Simple and widely understood.
- No extra token or key management required.
- Can provide both API and interface access.
Cons
- Credentials are highly sensitive and must be handled securely.
- Offers no fine-grained or delegated access.
- Frequent password rotation may disrupt integrations.
- Without MFA, exposure can compromise full access.
Best Practices
- Always transmit credentials over HTTPS.
- Avoid storing passwords in plain text; use secure vaults or encrypted storage.
- Encourage strong, unique passwords for API accounts.
- Use MFA wherever supported.
- Prefer username/password only for trusted internal apps or legacy integrations.
The sketchy retro route
Full control… and full of compromises. It works, but it’s like relying on a carrier pigeon to send your API requests, we have cleaner options.
Access tokens and refresh tokens
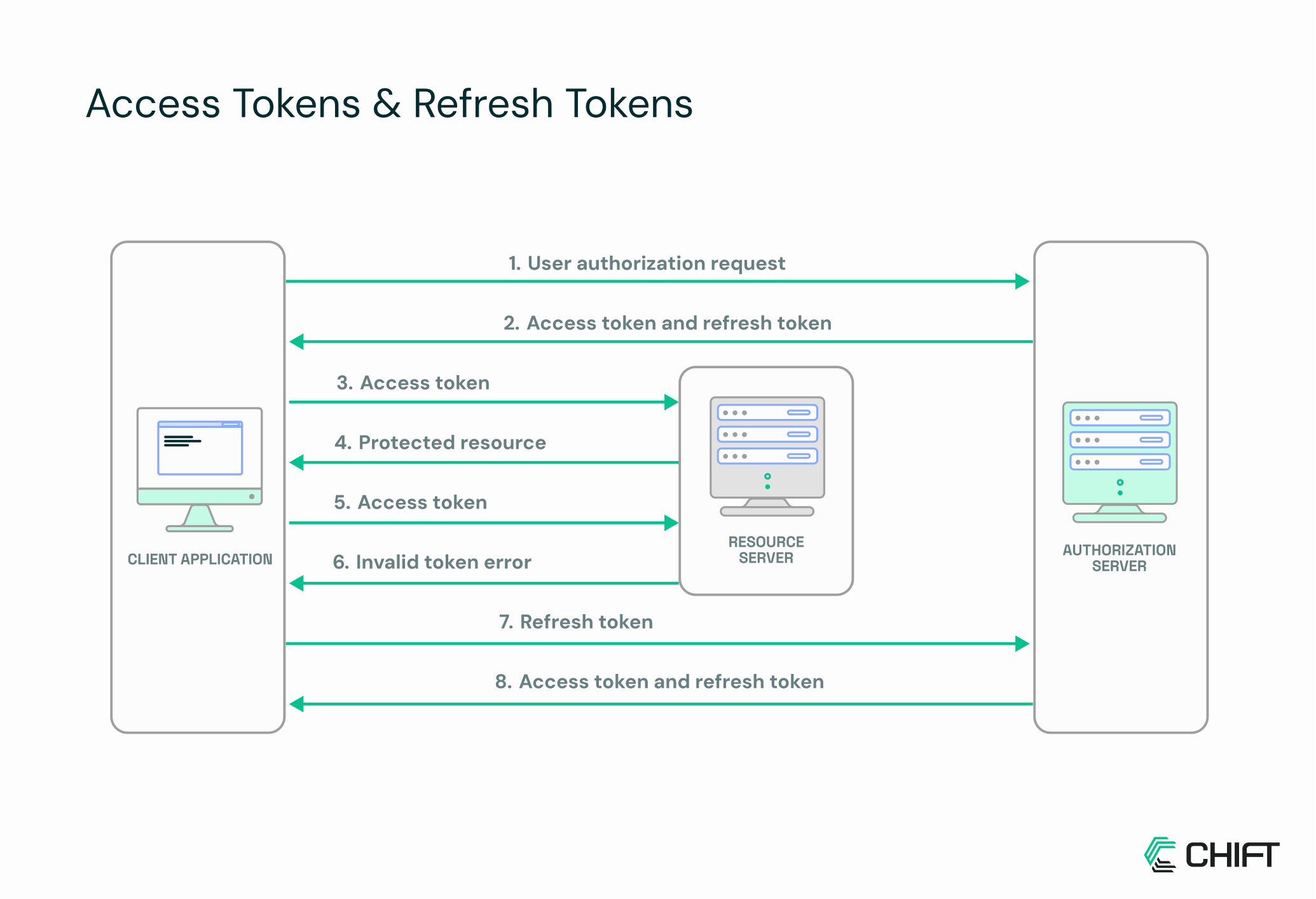
Some APIs follow a “full OAuth” flow with separate access and refresh tokens, but in practice, many financial and e-commerce platforms use a simplified approach. They provide a single long-lived token, which your app uses to request short-lived access tokens internally; effectively mimicking OAuth without exposing the user to repeated logins.
This setup balances ease of use and security: developers get token-based access without implementing the full OAuth dance, while short-lived access tokens still limit exposure if they leak. For integrations, whether connecting an online store to accounting software or linking a payment provider, this pattern keeps things smooth.
Pros
- Easier to implement than full OAuth flows.
- Still benefits from scoped, token-based access.
- Reduces user friction compared to classic login flows.
Cons
- Less standard than full OAuth; developers must handle token minting correctly.
- Long-lived “refresh” tokens need careful storage.
- Limited compatibility if migrating to full OAuth in the future.
Best practices
- Treat the long-lived token like a refresh token: store it securely on the backend.
- Mint short-lived access tokens for API calls whenever possible.
- Revoke and rotate tokens if there’s any suspicion of compromise.
- Validate token scopes often.
Smooth operator
Looks like one token, works like many: temporary access tokens handle your API requests quietly and efficiently.
Conclusion
There’s no single authentication method that fits every situation. API keys are quick and easy, username/password is familiar, and simplified token flows feel convenient, but each comes with its own trade-offs in security, flexibility, or scalability.
OAuth 2.0 stands out as the clear path forward for modern financial integrations: token-based, scope-limited, and designed to protect user credentials while keeping developer friction low. As platforms, from accounting and e-commerce to payment providers, connect more tightly, OAuth ensures safer, more flexible, and future-proof connections.
If all this sounds like a headache you’d rather skip, Chift normalizes and manages authentication for you so your users enjoy a seamless, often one-click activation experience.


.webp)
.jpg)
.jpg)





.webp)
.webp)
.webp)















.avif)



